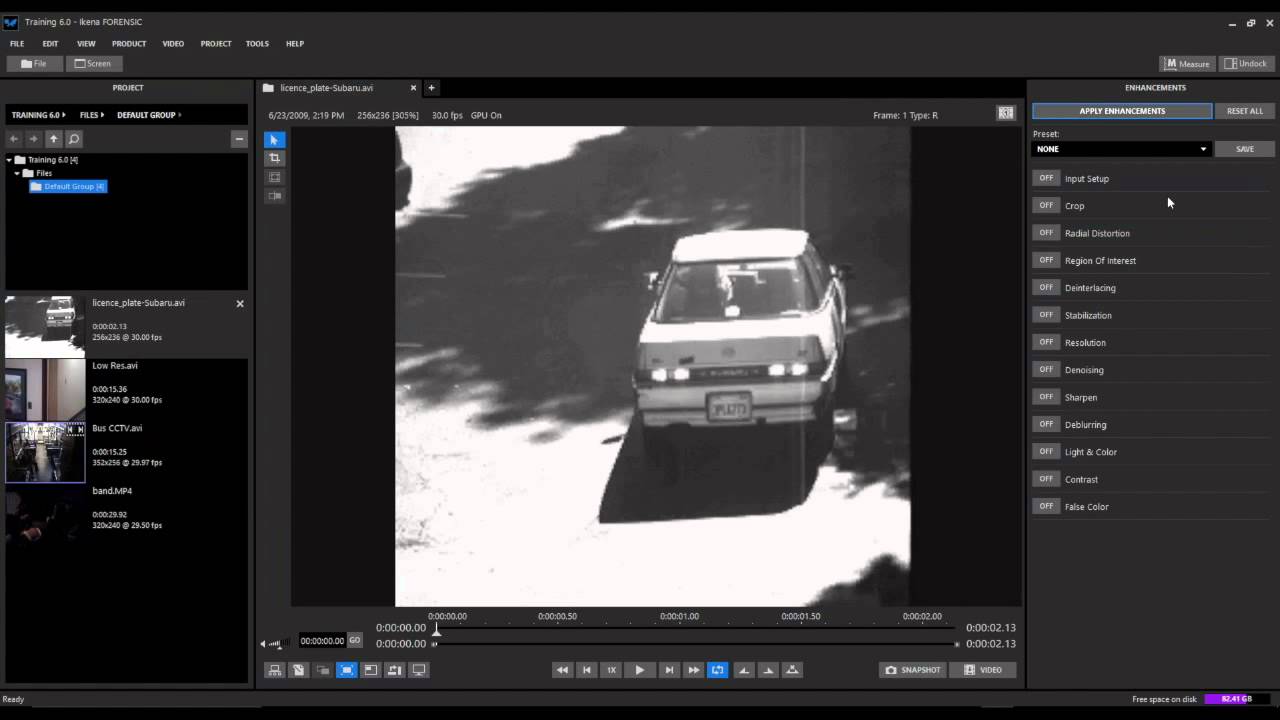
Forensic Image Analysis - ClearID Workflow not only provides you more than 20 image clarification Photoshop filters that are powerful, easy to use, and non-destructive to your original evidence, it also provides you a tabbed workflow interface that guides you through the image clarification process and automated scripts that apply SHA-1 hashing to your images. Imaging software creates reads the source evidence through the write blocker and creates a 'forensic image' on a destination device. While creating the forensic image the imaging software also calculates a digital 'fingerprint' (technically known as a 'hash signature') for the evidence and stores this signature with the forensic image.
Product Description
MacImager™ is a Mac OS X based drive imaging tool for securing evidence for further forensic analysis. Designed for the digital forensics and e-discovery professionals, the easy-to-use yet powerful tool allows investigators to secure evidence from drives or media in the form of disk images. MacImage is device and file system independent, and uses a proprietary fault tolerant acquisition to work around disk errors to obtain as much valid data as possible.
To support forensic needs of different forensic communities, MacImager supports MD5 hashing algorithm. Whether the drive or media is sound or faulty, MacImager is the only choice when it comes to forensics disk imaging.
MacImager disk imaging software uses a proprietary fault tolerant acquisition to work around disk errors to obtain as much valid data as possible. Whether the drive or media is sound or faulty, MacImager is the only choice when it comes to forensics disk imaging.
Complete device imaging: every sector of the device is copied. The software supports all file systems such as HFS, NTFS, FAT, FAT32, and Linux. MacImager works with USB key, PC disk, Linux disk, FAT32 disk, FLASH card, Digital Cameras, and almost any other media or file system that can be recognized in Mac OS X. Disk images created using the acquisition process with MacImager are saved in Apple's standard DMG format and can be opened and read by many standard applications such as MacForensicsLab or Cache Detective for further analysis of the data.
Imaging a damaged hard disk or storage medium with bad blocks. When ordinary data acquisition tools encounter hard disk with bad blocks, most will try to read the bad block data repeatedly, and ultimately abandon the imaging process when the bad blocks cannot be read. More over, in the event of hard disk with multiple bad blocks, using hard disk read-write head and trying to read bad data repeatedly may cause the hard disk to heat up and damage. MacImager uses a special algorithm that can effectively address sectors with bad data, and recovers as much data as possible.
Written specifically for Mac OS X, MacImager includes powerful features that give a user excellent flexibility in imaging a volume or a device:
- Image drive in device level.
- Proprietary fault tolerant acquisition works around disk errors to create disk image.
- Independent of operating system.
- Support high-speed interface such as USB 3 and Thunderbolt.
- MD5 HASH support.
- Images acquired are saved in open ISO standard and can be read by many Mac applications.
- Extremely easy-to-use interface. No special training necessary.
System Requirements:
- OS X 10.6 (Snow Leopard) or above
- Built for OS X Yosemite
- Intel based Macintosh
- Plenty of disk storage space
[Original post by Amanda Visconti. Minor updates in July 2018 to resolve outdated links and media.]
Last week, I wrote about how to forensically image the internal hard drive on a Mac laptop without needing to physically remove the drive. If your workspace doesn't have the necessary tools to follow that tutorial (a firewire cable, a firewire port on the Mac you're imaging, and a firewire port on a PC partitioned with BitCurator), we offer an alternative in this post.
Other Options for Imaging Mac Laptops
We recognize that you might not have the correct devices on hand to follow the instructions in the previous post. In that case, you may want to open the laptop to temporarily remove the hard drive for forensic imaging within the BitCurator environment, which means you'll need a cable that connects a hard drive to your imaging computer (probably a SATA cable). You can also opt to make a forensics image outside BitCurator and then import the image into BitCurator for exploration.
Note that the issue complicating this imaging process is specific to Mac laptops; Linux and Windows laptops wouldn't require target disk mode and the trouble that causes. Target disk mode works with other Macs (perhaps obviously) and Linux machines; I wasn't able to get a Windows machine to recognize the Mac laptop in target disk mode. I've read that commercial software called MacDrive (currently about $50 for use on one PC) will let you connect the a Mac in target disk mode to a PC, but this would not make the Mac drive also available in the Windows computer's BitCurator VM; unfortunately, VirtualBox is unable to take firewire input. It's possible you could get around this issue by using other virtualization software, but VirtualBox is the best free/open-source option.
That leaves us with using either a Mac or Linux machine to create our backup of the Mac laptop; in our example, I used a Mac to create the backups. We'll walk you through how to first lessen the risk of tampering with a laptop's insides by securing a forensic image outside of BitCurator.
Why Backup?
Opening up the laptop, removing the drive, and later trying to put everything back risks the laptop refusing to start or otherwise being damaged: maybe you break something, or can't get things to fit back together. If you don't have another way to gather a forensics disk image packaged with metadata about the imaging, though, opening the laptop up can be an acceptable risk. All computers fail eventually, and we'd rather have a good forensics disk image of the laptop now, than more years with the laptop working but no forensics image preserved. We thus recommend you forensically image the laptop's hard drive before opening it, or choose to create a forensics image with one of the non-BitCurator options discussed below and import the image into BitCurator. Opening up the computer is only necessary if none of these forensics imaging programs are right for you, your Mac laptop doesn't have a firewire port, or if you prefer to do all your forensic work inside the BitCurator environment. For either method, you'll need a firewire and another Mac (with a firewire port) on which to image the laptop.
Write Blocking
First, we need to protect the laptop from having the connected machine write back to it during the imaging process. This wasn't a major concern in our example as Larsen's laptop has already been explored by researchers at MITH—but it's good practice nonetheless, especially if you use a command-line imaging method, where a simple is-typing could accidentally erase your device. Our WiebeTech Forensic ComboDock works well for most write-blocking purposes, but it doesn't have the firewire input and output needed to work with a Mac in target disk mode. Tableau T9 Firewire Forensic Bridge is a hardware option that does accept both firewire input and output, but we didn't have one on hand. We thus used software write-blocking instead, installing Aaron Burghardt's Disk Arbitrator to protect the laptop.
A Forensic Disk Image
Begin by putting the Mac laptop you want to image into target disk mode:
- The laptop to be imaged (e.g. our Larsen laptop) should be turned off.
- Hold down the t key and turn the laptop to be imaged on.
- Continue to hold down the t key until the target disk mode image appears on the screen (see photo below).
You can now connect your firewire cable to both the laptop to be imaged and the Mac (or Linux computer) doing the imaging.
To create a forensics disk image, there are a variety of free and commercial programs that provide graphical interfaces for Mac and Linux, including MacOSXForensics Imager (Mac) and Guymager (Linux; note that Guymager is the imaging software BitCurator incorporates). Commercial options such as FTK Imager also exist. Almost any program that creates the image in an Encase (E01) or AFF forensic disk image format works, as these formats take a raw disk image and wrap metadata about the imaging around it. We haven't formally evaluated the effectiveness of any programs outside the BitCurator suite, though, so you'll want to check potential Mac forensic imaging software out yourself and explore the images they create within the BitCurator environment to make certain they captured your device correctly.
Alternatively, you can choose one of the following command line methods—but it's of utmost importance that you use a write-blocker with these, as mis-typing could erase your device:

Forensic Image Analysis - ClearID Workflow not only provides you more than 20 image clarification Photoshop filters that are powerful, easy to use, and non-destructive to your original evidence, it also provides you a tabbed workflow interface that guides you through the image clarification process and automated scripts that apply SHA-1 hashing to your images. Imaging software creates reads the source evidence through the write blocker and creates a 'forensic image' on a destination device. While creating the forensic image the imaging software also calculates a digital 'fingerprint' (technically known as a 'hash signature') for the evidence and stores this signature with the forensic image.
Product Description
MacImager™ is a Mac OS X based drive imaging tool for securing evidence for further forensic analysis. Designed for the digital forensics and e-discovery professionals, the easy-to-use yet powerful tool allows investigators to secure evidence from drives or media in the form of disk images. MacImage is device and file system independent, and uses a proprietary fault tolerant acquisition to work around disk errors to obtain as much valid data as possible.
To support forensic needs of different forensic communities, MacImager supports MD5 hashing algorithm. Whether the drive or media is sound or faulty, MacImager is the only choice when it comes to forensics disk imaging.
MacImager disk imaging software uses a proprietary fault tolerant acquisition to work around disk errors to obtain as much valid data as possible. Whether the drive or media is sound or faulty, MacImager is the only choice when it comes to forensics disk imaging.
Complete device imaging: every sector of the device is copied. The software supports all file systems such as HFS, NTFS, FAT, FAT32, and Linux. MacImager works with USB key, PC disk, Linux disk, FAT32 disk, FLASH card, Digital Cameras, and almost any other media or file system that can be recognized in Mac OS X. Disk images created using the acquisition process with MacImager are saved in Apple's standard DMG format and can be opened and read by many standard applications such as MacForensicsLab or Cache Detective for further analysis of the data.
Imaging a damaged hard disk or storage medium with bad blocks. When ordinary data acquisition tools encounter hard disk with bad blocks, most will try to read the bad block data repeatedly, and ultimately abandon the imaging process when the bad blocks cannot be read. More over, in the event of hard disk with multiple bad blocks, using hard disk read-write head and trying to read bad data repeatedly may cause the hard disk to heat up and damage. MacImager uses a special algorithm that can effectively address sectors with bad data, and recovers as much data as possible.
Written specifically for Mac OS X, MacImager includes powerful features that give a user excellent flexibility in imaging a volume or a device:
- Image drive in device level.
- Proprietary fault tolerant acquisition works around disk errors to create disk image.
- Independent of operating system.
- Support high-speed interface such as USB 3 and Thunderbolt.
- MD5 HASH support.
- Images acquired are saved in open ISO standard and can be read by many Mac applications.
- Extremely easy-to-use interface. No special training necessary.
System Requirements:
- OS X 10.6 (Snow Leopard) or above
- Built for OS X Yosemite
- Intel based Macintosh
- Plenty of disk storage space
[Original post by Amanda Visconti. Minor updates in July 2018 to resolve outdated links and media.]
Last week, I wrote about how to forensically image the internal hard drive on a Mac laptop without needing to physically remove the drive. If your workspace doesn't have the necessary tools to follow that tutorial (a firewire cable, a firewire port on the Mac you're imaging, and a firewire port on a PC partitioned with BitCurator), we offer an alternative in this post.
Other Options for Imaging Mac Laptops
We recognize that you might not have the correct devices on hand to follow the instructions in the previous post. In that case, you may want to open the laptop to temporarily remove the hard drive for forensic imaging within the BitCurator environment, which means you'll need a cable that connects a hard drive to your imaging computer (probably a SATA cable). You can also opt to make a forensics image outside BitCurator and then import the image into BitCurator for exploration.
Note that the issue complicating this imaging process is specific to Mac laptops; Linux and Windows laptops wouldn't require target disk mode and the trouble that causes. Target disk mode works with other Macs (perhaps obviously) and Linux machines; I wasn't able to get a Windows machine to recognize the Mac laptop in target disk mode. I've read that commercial software called MacDrive (currently about $50 for use on one PC) will let you connect the a Mac in target disk mode to a PC, but this would not make the Mac drive also available in the Windows computer's BitCurator VM; unfortunately, VirtualBox is unable to take firewire input. It's possible you could get around this issue by using other virtualization software, but VirtualBox is the best free/open-source option.
That leaves us with using either a Mac or Linux machine to create our backup of the Mac laptop; in our example, I used a Mac to create the backups. We'll walk you through how to first lessen the risk of tampering with a laptop's insides by securing a forensic image outside of BitCurator.
Why Backup?
Opening up the laptop, removing the drive, and later trying to put everything back risks the laptop refusing to start or otherwise being damaged: maybe you break something, or can't get things to fit back together. If you don't have another way to gather a forensics disk image packaged with metadata about the imaging, though, opening the laptop up can be an acceptable risk. All computers fail eventually, and we'd rather have a good forensics disk image of the laptop now, than more years with the laptop working but no forensics image preserved. We thus recommend you forensically image the laptop's hard drive before opening it, or choose to create a forensics image with one of the non-BitCurator options discussed below and import the image into BitCurator. Opening up the computer is only necessary if none of these forensics imaging programs are right for you, your Mac laptop doesn't have a firewire port, or if you prefer to do all your forensic work inside the BitCurator environment. For either method, you'll need a firewire and another Mac (with a firewire port) on which to image the laptop.
Write Blocking
First, we need to protect the laptop from having the connected machine write back to it during the imaging process. This wasn't a major concern in our example as Larsen's laptop has already been explored by researchers at MITH—but it's good practice nonetheless, especially if you use a command-line imaging method, where a simple is-typing could accidentally erase your device. Our WiebeTech Forensic ComboDock works well for most write-blocking purposes, but it doesn't have the firewire input and output needed to work with a Mac in target disk mode. Tableau T9 Firewire Forensic Bridge is a hardware option that does accept both firewire input and output, but we didn't have one on hand. We thus used software write-blocking instead, installing Aaron Burghardt's Disk Arbitrator to protect the laptop.
A Forensic Disk Image
Begin by putting the Mac laptop you want to image into target disk mode:
- The laptop to be imaged (e.g. our Larsen laptop) should be turned off.
- Hold down the t key and turn the laptop to be imaged on.
- Continue to hold down the t key until the target disk mode image appears on the screen (see photo below).
You can now connect your firewire cable to both the laptop to be imaged and the Mac (or Linux computer) doing the imaging.
To create a forensics disk image, there are a variety of free and commercial programs that provide graphical interfaces for Mac and Linux, including MacOSXForensics Imager (Mac) and Guymager (Linux; note that Guymager is the imaging software BitCurator incorporates). Commercial options such as FTK Imager also exist. Almost any program that creates the image in an Encase (E01) or AFF forensic disk image format works, as these formats take a raw disk image and wrap metadata about the imaging around it. We haven't formally evaluated the effectiveness of any programs outside the BitCurator suite, though, so you'll want to check potential Mac forensic imaging software out yourself and explore the images they create within the BitCurator environment to make certain they captured your device correctly.
Alternatively, you can choose one of the following command line methods—but it's of utmost importance that you use a write-blocker with these, as mis-typing could erase your device:
- If you're very knowledgeable about using the command line, you may already know how to use dd or dcfldd.
- The ForensicsWiki has a detailed tutorial on 'Acquiring a Mac OS System with Target Disk Mode' that uses dd and other commands to create a .dmg image, plus instructions on converting the .dmg to an Encase format.
- 'Macintosh Forensics: A Guide for the Forensically Sound Examination of a Macintosh Computer' by Ryan Kubasiak offers alternative instructions for using dd (use the hyperlinked table of contents to jump to the 'Imaging a Target Macintosh' section starting on page 25).
Opening the Laptop to Remove the Hard Drive
Forensic Image Enhancement Software
After following these steps to make a forensic image of your laptop, you can either opt to import the forensic image into BitCurator and explore the image there, or choose to temporarily remove the hard drive in order to image it directly through BitCurator. If you choose the latter path, you'll need to search for instructions like these that show how to open your particular model of Mac. If possible, use a guide with many photos to show you how to carefully open, remove, and replace the Mac laptop's hard drive. I've found that sites dedicated to DIY fixing and making, such as iFixit and Instructables, offer good community-moderated tutorials on opening up computers.
In a future post, I'll discuss what I found while exploring the Larsen laptop disk image using BitCurator. Send us your suggestions for other difficult-to-image use cases, and we'll cover them in future posts!
Forensic Image Enhancement Software Mac Mojave
Amanda Visconti is a MITH graduate research assistant on the BitCurator project, where she creates user-friendly technical documentation, develops and designs for the web, and researches software usability. As a Literature Ph.D. candidate, she blogs about her digital humanities work regularly at LiteratureGeek.com.
